There are various speculations online whether Advanced Mac Cleaner is legitimate cyber security software for Macs or it is just an unwanted software that tries to scam users and charge them for nothing?
Probably the best way to find it out is to take a look at the feedback from users themselves. For instance, there is a question on official Apple discussions forum about Advanced Mac Cleaner and continuous advertisements suggesting that one should install it:
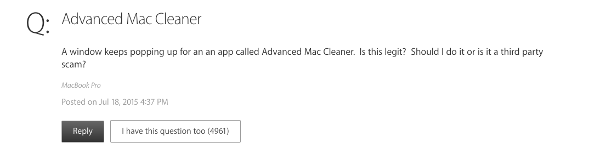
As you can see, almost 5000 other users noted that they also have this question, so you can suspect that this software is promoted really intensively.
Majority of users replied that this software is just a scam and you should never even think about getting it. Let’s take a look at why it is so.
Advanced Mac Cleaner can’t keep their promises
This particular piece of software is supposed to speed up your Mac and clean it from trash files that you don’t really need. It sounds realistic – there are more than a few options of various free and paid tools that can do that for you, such as Malwarebytes Anti-Malware for mac or Adwaremedic for Mac. However, Advanced Mac Cleaner is not in this list of legitimate applications for your Apple device.
As described by cyber security researchers at 2-viruses.com, Advanced Mac Cleaner is categorised as PUP (potentially unwanted program) and “there are tons of negative reviews of this application online and most of them are regarding the way this application is distributed”.
First thing that you are not going to like – the way it is installed on your computer. Most of the time this program is suggested after the warning message that your Mac is infected is displayed. It is a straight forward lie – they just try to convince users that their computers are infected and suggest a “solution” to this problem.
More to that, Advanced Mac Cleaner is not functioning as it should. it will barely remove any trash or speed up your computer. Instead of that, you will be offered a live tech-support which will cost you money. While the program itself is free, they monetise it selling this support feature. The truth is 9 times out of 10 you don’t really need support.
So is it worth installing Advanced Mac Cleaner? Definitely not. It might not damage your computer, but it will definitely try to lure money and display you information that is not correct.